This blog post will show two ways to join an Azure Virtual Machine to Azure Active Directory.
Once a machine is joined to Azure AD, it can be managed and secured using Microsoft Intune MDM and protected using Defender for Endpoint. We can also control access to the VM using a single identity provider (Azure AD).
Method 1 – Use Azure VM Identity Feature
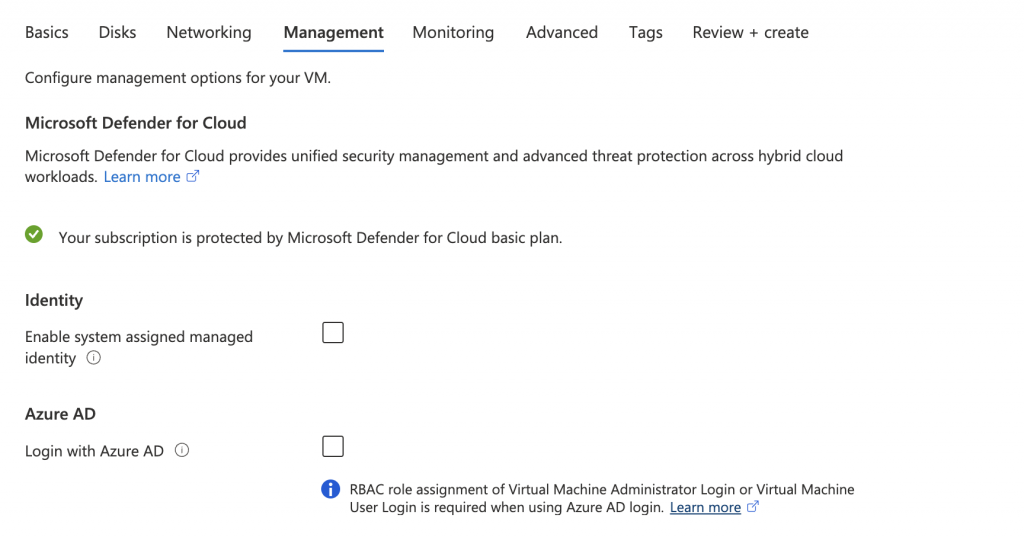
When you set up your Azure VM from the portal or IaC tools, the management tab has an Identity option. If you tick the Azure AD option, Azure AD users can log in to the VM using their Azure AD credentials.
The only issue with this option is that the client that connects to the VM needs to be Azure AD joined. This can be an issue if your machine is not joined to Azure AD or you are developing a solution.
We think that this option is not suitable for everyone. However, it is more secure compared to the next option.
Method 2 – Join Azure VM to Azure Active Directory
If the first option does not work for you because you prefer not to join your client machine to Azure AD, you use this option.
To use this option, create an Azure VM using the portal or an IaC tool like Terraform or ARM without ticking the Azure AD identity option.
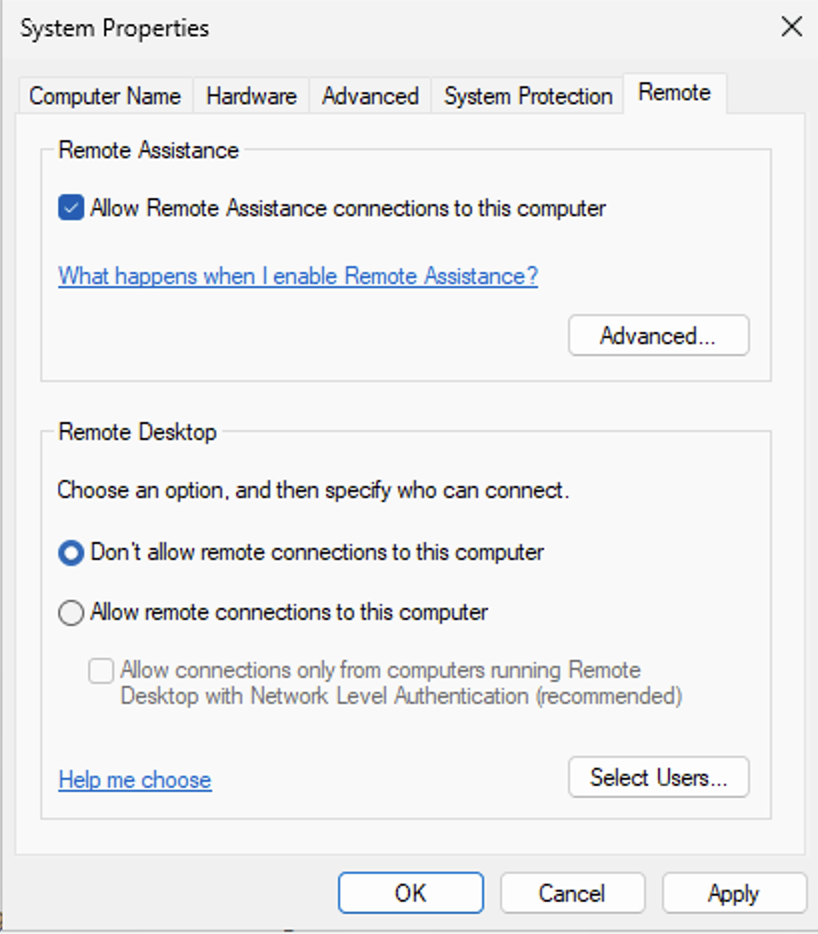
Disable NLA (Network Level Authentication) on the VM by opening the System Properties (sysdm.cpl)
Click on Remote
Un-tick “Allow connections from computers running…”
After NLA is disabled, Join the machine to Azure AD using our blog post below:
Join Windows 11 to Azure Active Directory
Once the machine is joined to Azure AD, you can log in using the following login format.
azuread\user@yourdomian.com
It is crucial you use the AzureAD\ format before your user name