Active Directory (Azure AD) is a cloud-based identity and access management service that provides an easy way for organizations to manage the identities of their users.
Azure AD enables you to manage user access to your web applications, mobile apps, and other resources that are hosted on Azure or in your organization’s datacenter. In this article, we will show you how to configure users consent to applications in Azure AD.
Application Consent
Application consent is the permissions that an application needs in order to access Azure Active Directory resources. Azure Active Directory administrators can configure these permissions for users and groups. When an administrator configures application consent for a user, the user is prompted to consent to the application.
If the user consents, Azure Active Directory provides the application with the permissions that were configured. If the user doesn’t consent, Azure Active Directory denies access to the application. Administrators can also configure group-based consent, which allows a group of users to give or deny permissions to an application by using Azure AD groups.
Allowing users to consent to application requests to access data in Microsoft 365 is very risky and can expose the entire tenant to vulnerabilities.
Azure Active Directory allows administrators to set up a process to request admin consent to applications using a review workflow.
Create Admin Consent Process
To create an admin consent process, open the Azure Active Directory console -> Enterprise applications > User settings.
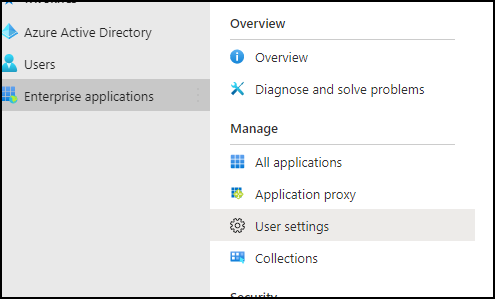
In the User Settings page, select Yes next to “Users can request admin consent to apps”
Under the review type, select a group or a single user who can approve the request under the review type. Review the other settings if you need email notifications.
The last section allows administrators to pre-approve applications to users.

For more Azure AD posts, please visit the category page.