When managing users in Azure AD it’s recommended to have a password policy in place however sometimes the best password policy cannot prevent users from using well-known passwords.
Today, I will show you how to enable the new Azure AD password protection and Smart Lockout feature that will prevent users from using an easy password like P@ssw0rd and other well-known passwords.
Password Protection and Smart Lockout allow to do 3 things:
- Protect accounts in Azure AD and Windows Server Active Directory by preventing users from using passwords from a list of more than 500 of the most commonly used passwords, plus over 1 million character substitution variations of those passwords.
- Manage Azure AD Password Protection for Azure AD and on-premises Windows Server Active Directory from a unified admin experience in the Azure Active Directory portal.
- Customize your Azure AD smart lockout settings and specify a list of additional company-specific passwords to block.
Requirements
To enable the new features, you will need to have an Azure AD Premium 1 or above licenses.
In my case, I have Enterprise Mobility + Security E3 licenses which gives me Azure AD Premium P1
Get Started
To enable Password Protection, I will access Azure AD from the Azure Portal and click on Authentication Methods -> Password Protection

In the password protection screen, I have the option to change Lockout threshold and the Lockout duration.
The main feature is the Custom banned passwords where I can enable it and add password I want to ban on top of the 1 million password that is already banned from Azure AD password protection service

All I need to do is click yes and type the banned passwords
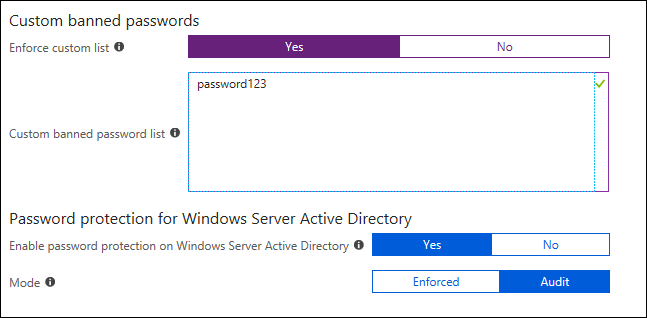
In hybrid mode, I have the option to install an AD agent that will enable the feature for my on-prem AD.