This blog post will show how to enable a 14 days grace period for setting up Multi-Factor authentication for new Microsoft 365 users.
By default, when MFA is enabled either manually, using security defaults or using conditional access, users have to set up MFA when they first log in to Microsoft for the first time.
In some cases, this can be counterproductive; therefore, an MFA grace period can give the users a few days to set up their MFA.
Enable Grace Period
To enable a Grace period for MFA, you will need an Active Directory P2 license and enable an Identity protection policy.
To enable the policy, Open Azure Active Directory -> Identity protection ->
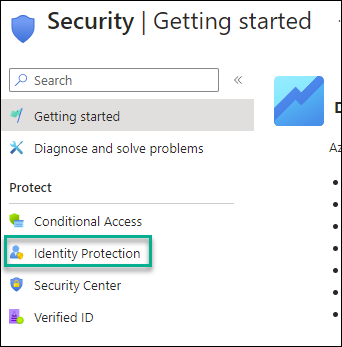
Click on the Multifactor Authentication registration policy
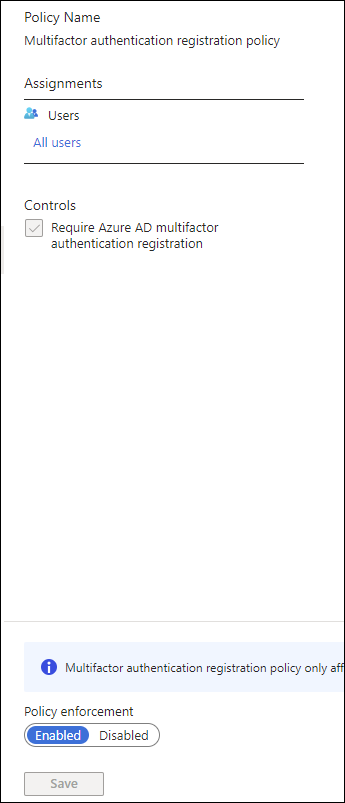
In the Controls section, tick the box
Require Azure AD Multifactor authentication registration
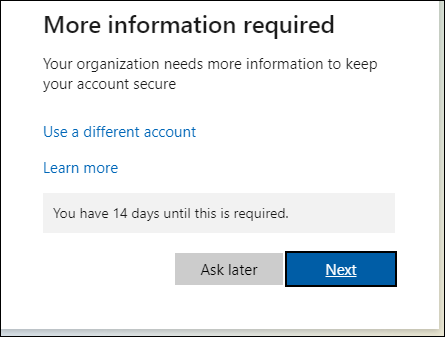
When users log in for the first time, they will see the following message