In this blog post, we’ll explore how you can exclude and disable Azure AD-joined VMs with conditional access policies.
What is Conditional Access?
Conditional access is a feature of Azure AD that allows you to define access policies based on certain conditions, such as the user’s group membership, device state, or network location. These policies can be used to restrict access to sensitive resources, such as Azure AD joined VMs, to only authorized users and devices.
Manage Azure AD Joined VMs Conditional Access
The problem with MFA and Azure AD Joined VMs is that in order for MFA to work the clients need to use certificate-based login and if a certificate is not available users can’t log in to the VM.
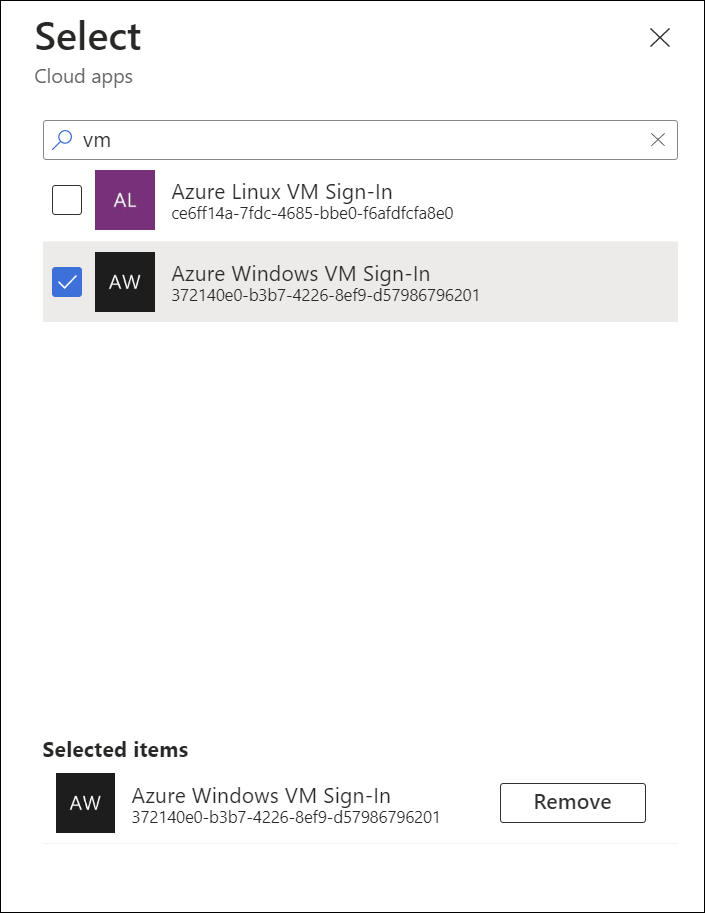
To disable MFA when trying to log in to Azure AD Joined VMs, Microsoft made a cloud app available to tenants where they can control access and setup conditional access.
The App name is Azure Windows VM Sign-in. To exclude it from MFA requirements edit your existing MFA conditional access rule and exclude the app.